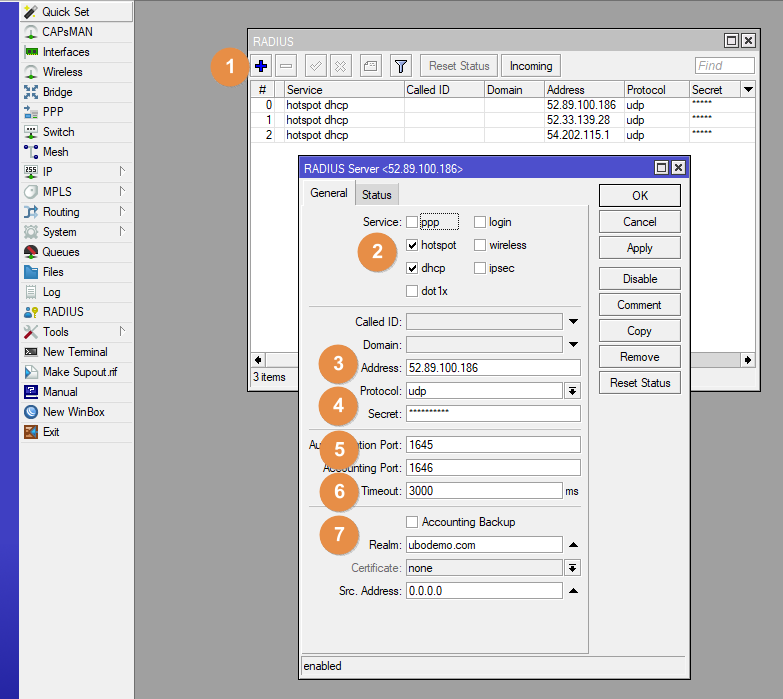
This section configures your Mikrotik router to communicate with the Visp.net HyperRADIUS servers.
Critical Note: For the Multi-ISP setup, you must use these proxy servers: 52.37.68.81 and 52.11.17.135.
Primary
- Click Radius (left) and click (+) symbol to add a radius server.
- Under the General tab, select Hotspot, PPPoE, or DHCP for Service
- Address: 52.89.100.186
- Secret field: Contact Visp Client Success for the secret keys.
- Auth port: 1645 and Acct port: 1646
- Timeout: 3000ms
- Realm: yourdomain.ext (e.g. ubodemo.com)
Secondary
- Click Radius (left) and click (+) symbol to add a radius server.
- Under the General tab, select Hotspot, PPPoE, or DHCP for Service
- Address: 52.33.139.28
- Secret field: Contact Visp Client Success for the secret keys.
- Auth port: 1645 and Acct port: 1646
- Timeout: 3000ms
- Realm: yourdomain.ext (e.g. ubodemo.com)
Backup / Fail-Over
- Click Radius (left) and click (+) symbol to add a radius server.
- Under the General tab, select Hotspot, PPPoE or DHCP for Service
- Address: Select from options below
- Secret field: VISP
- Auth port: 1645 and Acct port: 1646
- Timeout: 3000ms
- Realm: yourdomain.ext (e.g. ubodemo.com)
Options for the backup server:
- 104.197.14.68 – Unlimited
- 52.36.172.140 -150MB/150MB
- 104.197.99.33 – 15MB/10MB
- 23.236.57.151 – 10MB/5MB
- 104.197.22.129 – 5MB/3MB
- 52.11.200.62 – 3MB/1MB
- 146.148.105.15 – 20MB/10MB for Old DHCP authentication only
Note: Make sure that the backup server should always be the least priority by putting it at the bottom.